Recently I was engaged in a project for NSX Brownfield deployment and the requirement was to migrate the citrix environment to VMware Horizon View desktops.
So the challenge we had was to find out what is in use by the Citrix VMs in the existing environment from the service/port perspective so it will be easier to find out the communication path between twoVMs (for test for now) but it can be scaled all the way to the cluster level if needs to.
So there are few ways this can be achieved and I will cover the same in the series of 3 parts.
1) Using ARM (Application Rule Manager) which will be covered in this post
2) Using vRNI (vRealize Network Insight) which will be the next post
3) Using LI (vRealize Log Insight) which will be the last post of this series
So lets get started.
We are running the latest NSX Manager version 6.3.1.
Now I assume that the readers are familiar with NSX Manager and other components of VMware vSphere as I will be using the terminologies quite frequently and also the acronyms of the same.
So once you go to Networking and Security and you need to click on Flow Monitoring to see the option of application Rule Manager
Im showing here the screen shot of the same.
So now lets dig deeper in to ARM.
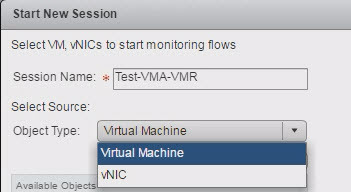
lets say I want to know the flows between two VMs so I will start with New Session and then give a name to the session.
Next option is to select the source and here you have only two options to choose from as a Object Type
1) Virtual Machine
2) vNIC
So I will go with VM and provide a name of the VM.
Thats the only thing you need to provide and once you click OK then it will start gathering the flows from the VM.
Now click Stop to finish collecting the flows and once you highlight any flows under the View Flows option then you will see two options under Actions.

So either you can hide records or you can create a Firewall Rule based on the flow captured.
After I selected Create Firewall Rule, then I will go to the tab "Firewall Rules" and check what rule is created.
You can create multiple sessions and just select the drop down to see/view specific Flow details about a particular session.
Name the session properly so you can see what you have captured. In the above screen shot as you can see I've given the name tst-h-ic-blk which I provided to find out the icmp block for horizon and the rule is test rule.
You can keep the name with the function of the VM/server you are going to create the firewall rule for, so it will be easier to understand take actions on the particular rule set.

Once you create the rule then you need to go the Firewall Rule tab and publish it and it will be immediately come in to the effect. Which you can verify under Firewall section on the left.

So as you can see, it will be added as a new Section to give the name to the rule properly so it will be meaningful.

Now from the product use perspective this will be a trouble when you have to find out the traffic patterns on a large environment (having no other options of at the cluster level or host level options) so you have only one choice of finding out per VM basis and then go thro each flow collected and create the rule/s.
May be I can suggest a feature request to VMware about incorporating other options when dealing with multiple items and have a single option to create Firewall rule / rules based on the collected flows. This can be based on the at the Data Center/ Cluster Level which can be considered in aggregation of all the flows captured.
It will help the Admin of the environment to allow the default communication ports which got captured after running the flow capturing for enough duration which will allow to capture all possible traffic coming from X and going to Y or Z.
Hoping that in next version this improvement will get incorporated to ease the process of utilizing only ARM to recommend the rules and go with the same.
Hope this helps.
In Next post I will cover vRNI to find out how you can utilize the same to create Firewall Rule/s.
Please share and care.
Thanks for your time.

